Sage People integrations to Microsoft 365 have been designed with security in mind. This section outlines the security features used by the integrations, and the secure service architecture that underpins them.
Session management
Our Microsoft 365 integration uses the OAuth 2.0 authorization standard to allow Sage People to connect securely to the Azure infrastructure. The information flow is outlined below.

For Microsoft Teams integration, a Sage Digital Experience service layer, hosted in the USA, securely links your Sage People organization with your Azure account, and manages user session information for the Teams digital assistant.
-
When a user makes a request that requires access to their Sage People account, the digital assistant prompts them to sign in. Sign in to the user's Salesforce organization is managed by the Digital Experience service layer.
All traffic from Microsoft Azure to the service layer is encrypted and authenticated by the Microsoft identity platform as an OAuth 2.0 session.
-
When a user signs in, the user's Azure email address is checked against the SSO registration database. This database retains the email addresses and custom domain for active users of the Teams integration, enabling seamless single sign-on to the user's Salesforce organization. The SSO registration database is stored in the Sage Digital Experience service layer, and updated daily according to the MS Teams SSO Registration Scheduled Time package setting.
-
On successful login, the Sage People Salesforce connected app issues an access token and refresh token to authenticate the user session. Tokens are encrypted and stored securely in the service layer.
Sessions are managed by the service layer. When the access token expires, the refresh token is used to re-authenticate the session and retrieve another access token.
If the service cannot obtain a new token for any reason, the user is signed out of the app and must re-authenticate using their credentials.
If the user signs out of the Teams app, the refresh token is expired and any sessions associated with the token are revoked.
- Requests in the digital assistant that require access to a user's Sage People account are handled by the service layer. All requests from the digital assistant are uniquely identified and authenticated by the Microsoft identity platform.
- Requests to your Sage People organization use a dedicated REST API. The API performs checks to ensure that the user has the required permissions and that requested data is enabled for Microsoft Teams integration. The API calls WX business logic to access team member self-service features.
For Microsoft Outlook integration, Sage People connects to the customer's Azure infrastructure using an app registered in their Microsoft identity platform that authenticates Sage People and grants permission for the service to access users' Outlook calendars on their behalf.
-
When a user enrolls for Outlook integration (time off) or schedules an interview for the first time (Recruit), the service retrieves an access token and refresh token via OAuth 2.0. These tokens are encrypted with AES-256 encryption and stored within Sage People.
- Subsequently, when an absence request is approved or a Recruit interview is scheduled, an OAuth 2.0 access token is retrieved from Active Directory via the refresh token flow, unless a valid access token already exists for the user.
- The Sage People organization sends an API request to the Microsoft Graph API using the OAuth 2.0 token from the previous step as the authorization header. Using the permissions delegated to the Sage People application via the Azure app registration, Outlook calendar events and invitations are created for the team member, manager, or interview participants.
- Refresh tokens will expire if you don't use then within 14 days. A scheduled job within the calendar package runs each day, and triggers a batch job: UpdateAuthTokensBatch. The batch job checks for any tokens you haven't updates within the last seven days, and calls the MS Token endpoint to exchange them for new tokens. This means refresh tokens will remain active and users won't be required to re-enroll. This includes times when the users haven't used the integration for more that 14 days.
Stored data
The Microsoft integration to Teams and Calendar sends data between Salesforce and Microsoft Azure using API requests. API calls to the Sage People app for Microsoft Teams are processed by the Digital Experience public cloud service layer, which is hosted in the USA, and is managed by Sage. API calls to the customer's Azure infrastructure for Calendar integration do not use this service layer.
Session information such as the access token and refresh token required for authentication are stored securely within the service layer using AES-GCM-256 encryption. Email addresses for users registered for SSO are stored in the service layer to enable seamless login to Sage People through the Teams app.
Absence information retrieved from Sage People is processed and stored by this service layer, and sent to your Azure infrastructure, secured by the Microsoft identity platform.
The Azure infrastructure is managed by the customer.
Remote access revocation (Teams app)
System administrators can revoke active user sessions, and prevent users from signing in to the app by revoking app permissions using the Setup section of the HR administrator portal.
To remotely end the user's session (for example, if the team member's device is lost or compromised):
-
Go to Setup > Users > Users.
-
Select the name of the user whose session you want to revoke.
-
Under OAuth Connected Apps, find the active Digital Assistant Prod session and select Revoke.
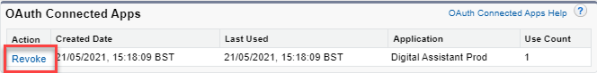
The user's access and refresh tokens are removed, and the user is required to log in again before accessing information from Sage People.
To prevent a user from logging in using Teams, remove the Sage People MS Teams fta permission set for the user.